Projects
Villan Security Portfolio Website
This site is more than a résumé; it's a full cybersecurity showcase, built from scratch using GitHub Pages, Jekyll, and the Spectral theme. Designed for clarity, stealth aesthetics, and real-world engagement, the site incorporates personal branding, red/blue team content, project documentation, and embedded detection mechanisms. It's both a storytelling platform and a live operational artifact.

- Tech Used: GitHub Pages, Jekyll, Cloudflare, Zoho Mail, Discord Webhooks
- Custom design and theme modification to align with blue/black/silver brand identity
- Built-in stealth canary trap using Cloudflare Workers and Discord alerting
- Modular content structure for ongoing project expansion and visual storytelling
- Balances personal narrative with professional expertise and real-world detection logic
Stealth Web-Based Canary Trap
This project implements a passive, stealth-based canary trap using a 1x1 transparent image embedded in a public-facing cert showcase. The trap silently triggers when a visitor loads the page, logging metadata such as IP, User-Agent, and Referrer. Real-time alerts are sent to Discord, and traffic is enriched through external APIs to extract ASN, geo-location, and abuse reputation.
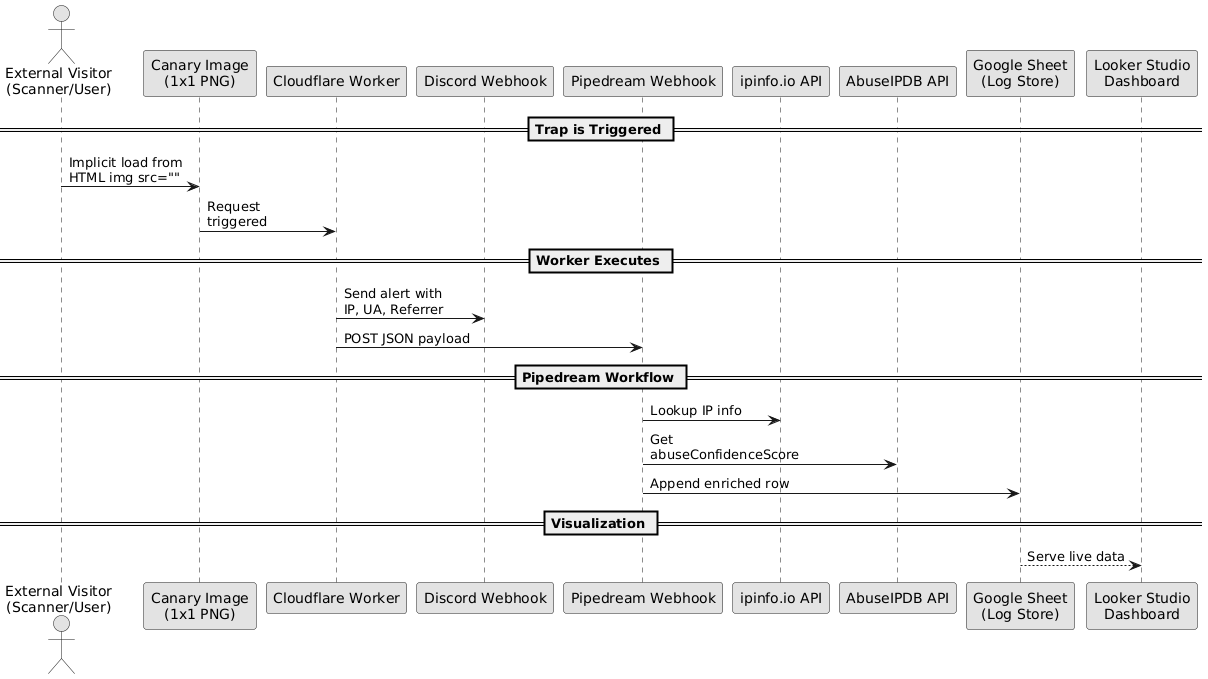
- Tech Used: Cloudflare Workers, Discord Webhooks, Pipedream, ipinfo.io, AbuseIPDB, Google Sheets, Looker Studio
- Detection: Triggers on image load — even from headless browsers or scrapers
- Enrichment: Adds ASN, Country, and Abuse Confidence Score for every hit
- Logging: Centralized log to Google Sheets for retention and analysis
- Visualization: Live Looker Studio dashboard tracks activity trends over time
This trap runs silently on public pages and provides visibility into reconnaissance behavior from scanning infrastructure and opportunistic threats.
Social Media OSINT Dashboard
This project combines real-time social media scraping, AI-driven sentiment analysis, and visual reporting to track public chatter around a target organization or topic. Built with Python and Streamlit, it ingests Twitter, Reddit, and RSS news content and generates dashboards, word clouds, keyword charts, and PDF reports. Sentiment scoring leverages GPT-based language models for nuanced analysis across platforms.
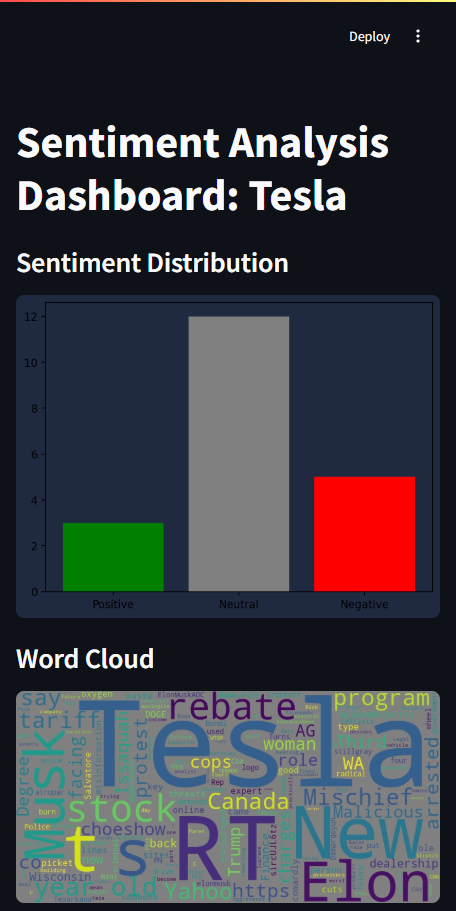
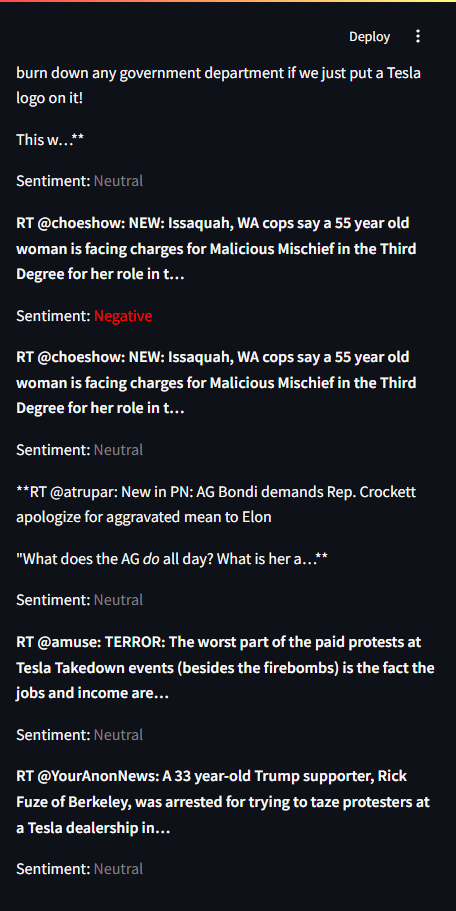
Note: This dashboard displays OSINT findings using publicly available data. Content shown here is for demonstration purposes only and does not imply affiliation.
- Tech Used: Python, Streamlit, OpenAI GPT, Reddit/Twitter APIs, BeautifulSoup, FPDF
- AI-powered sentiment classification using OpenAI’s GPT model
- Generates visual summaries, PDF reports, and interactive dashboards
- Designed for threat intelligence, brand monitoring, or executive insight
Capture the Flag Participation
I actively participate in national and platform-based CTF events to sharpen my technical skills and test myself against evolving challenges. These competitions span reverse engineering, forensics, scripting, exploitation, and real-world threat emulation. While scoring points is great, I focus on learning new techniques and reflecting on what I could apply to blue team operations.
- Participated in picoCTF 2025 — solved Linux privilege escalation, XOR crypto puzzles, and logic flaws under time pressure
- Completed US Cyber Challenge: Cyber Quest 2025 — demonstrated core skills in secure coding, threat analysis, and policy evaluation
- Maintain internal notes/playbooks for lessons learned and detection correlations
- Focused on bridging offensive challenge techniques with defensive detection thinking
Coming Soon: Adversary Simulation Lab
I'm building a containerized purple team lab using Docker to simulate adversary behaviors, validate defensive coverage, and test detection logic. The lab integrates both offensive and defensive components — from Cobalt Strike simulations to Sysmon and ELK log analysis — allowing me to iterate quickly and tune detections in a controlled, modular environment.
- Dockerized infrastructure for red team tooling and defensive telemetry collection
- Focused on real-world tactics: credential access, lateral movement, and persistence
- Mapped to MITRE ATT&CK for transparent detection alignment and tuning
- Built to support CRTO preparation, detection engineering, and purple team development